Safe Links
The purpose of this policy is to add a layer of protection to links both in received email and within other Microsoft applications such as SharePoint, OneDrive, and Teams.
Warning
Note that links blocked by safe links, such as domains specified in the tenant allow/block list are only blocking links within Microsoft applications. If you want to block links for a specific website, you should likely also add a block indicator in MDE or unsanction the application in MDCA or users could potentially extract the URL and access the URL/domain anyway.
Considerations before deployment
Note that unlike anti-phishing, anti-spam, and anti-malware, the "default" policy, known as "built-in protection", is not modifiable, and it is difficult to find how this policy is configured. For this reason it is advisable to make a custom policy targeting all of your domains to be your new "default" policy. You will be able to modify it and see its protections.
Policy Configuration
This policy is pretty basic and straightforward, a pilot policy is perfectly fine but usually changes you are making are chances to protect your users and not up for much debate.
Scoping users, groups, and domains
Pay attention to the conditions on custom policies, they are evaluated together because of the AND statements. If you put a user and a group, the user must be a member of the group and anyone else who is a member of that group will not be included in this policy unless they are listed on the user list.
Enabling this checks URLs for known malicious links and quarantines them.
Apply Safe Links to email messages sent within the organization
Enabling this protects internal email messages as well and is recommended.
Apply real-time URL scanning for suspicious links and links that point to files
Microsoft does not give much detail about this, it seems to expand protections to not just URLs but also downloadable content.
Wait for URL scanning to complete before delivering the message
This is only available if the above option is enabled and would be recommended.
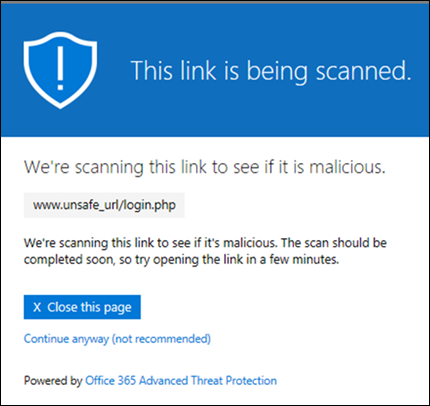
Do not rewrite URLs, do checks via Safe Links API only
The wording here is a bit confusing, but the recommendation is to have this off.
With this setting disabled, Microsoft rewrites all URLs and they will be prepended with this https://nam01.safelinks.protection.outlook.com where the nam01 is the data center and can be different. If using the Outlook client this does still show the original URL in a readable format when you hover over the link. The rewritten URL will show in the bottom left corner though.
Why is this important or useful you may be asking. Without rewriting the URL, the URL is only scanned at the time the email was received and not at the time of click! If using an official Microsoft email client such as Outlook the link is rechecked at the time of the click even when not rewritten. But this is not going to be the case for a non-Microsoft client such as iOS Mail.
So to ensure the link is always rescanned before a user access it keep this setting to off.
Do not rewrite the following URLs in email
Generally it is best to keep this list to a minimum but if you own the domain that would be acceptable to put in this list.
Other examples of URLs that may need to be in here are:
- Qualtrix URLs
- This is a survey tool and sometimes the URL rewrite can break parameters your data team may be using to pre-populate data.
- URLs that have a lot of redirects
- I don't see this an issue very often, but sometimes a webpage won't load if there are too many redirects, this is adding a redirect, so that is a scenario where you may add an exception I have found on occasion.
Teams
This works the same as email but because you are using a Microsoft client URLs are not rewritten and are just scanned at time of click against a list of known malicious URLs.
Office 365 Apps
This works the same as email but because you are using a Microsoft client URLs are not rewritten and are just scanned at time of click against a list of known malicious URLs.
Track user clicks
Enable this setting, this is a great tool to help you track down users who may have visited a phishing website. With Defender, you can easily go to a URL entity page and determine who has clicked the link. You may not know if they gave away credentials, but a password change is in order for these users!
Let users click through to the original URL
This option is best left disabled so user's can't access malicious sites.
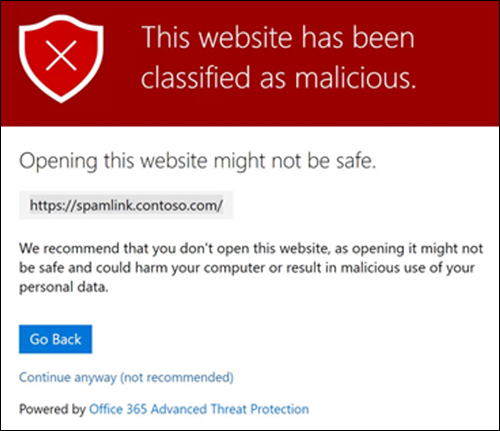
Display the organization branding on notifications and warning pages
This setting is recommended, and it uses the M365 Theme not the Azure/Entra ID branding. It is best to apply branding where possible.
Use custom notification text
Allows you to add a custom message to the warning displayed by this policy. They can even be translated to other languages if you enable that feature.